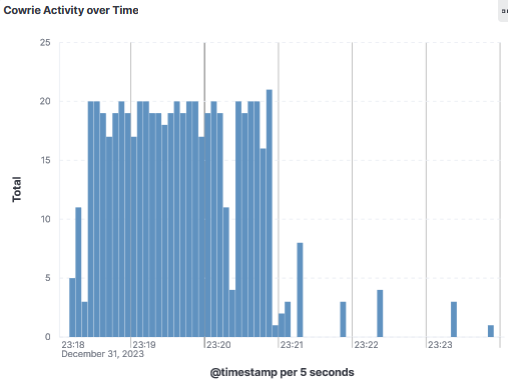
On the 31 Dec 2023, after trying multiple username/password combination, actor using IP 194.30.53.68 successfully loging to the honeypot and uploaded eight files where 2 of them are protected with a 7zip password (updates1.7z & updates2.7z). Some of these files have been identified to be related to the Prometei trojan by Virustotal. The file sqhost.exe [6] was last found by Talos [7] used with the Prometei botnet as a trojan coin miner.
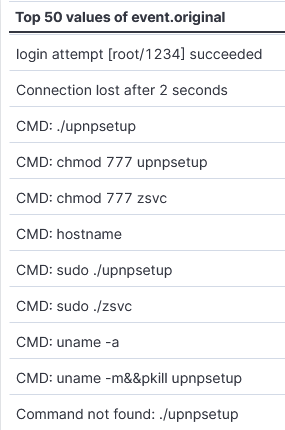
Some of the commands run by the actor after successful login.
The files uploaded to the honeypot are a combination of Windows and Linux executables.
Indicators of Compromize
7z.exe: ac9674feb8f2fad20c1e046de67f899419276ae79a60e8cc021a4bf472ae044f
7z.dll: a1e1d1f0fff4fcccfbdfa313f3bdfea4d3dfe2c2d9174a615bbc39a0a6929338
rdpcIip.exe: f4ac4f735b9ff260a275734d86610dccb8558d1a54c6d6a78a94c33b6aaf6e39
sqhost.exe: 7affd78df02298ce6e779833bb4f222193e65acf05488de5ba8c5388a3dd8e89
upnpsetup: 0ca3a4c2800f9454cdcbb8398a7ec97b00f90f4234c7c5e48e206a8352d86750 -> ELF 64-bit LSB executable
updates1.7z: 608b2c8220a595a9766e2fdc5c91899dda635f97bc505e1a41e523aaddb11652
updates2.7z: 6f39d02f27e3241224bb16e4753091b9d4ae2b4d0108a3fde2e3ebad0e1627bf
zsvc: d470e24adff149f1cb6710d2a005d8c07693ab0159de7cdc5e661c4879e2db58 -> ELF 64-bit LSB executable
194.30.53.68 correo.progecobilbao.com
[1] https://www.virustotal.com/gui/file/f4ac4f735b9ff260a275734d86610dccb8558d1a54c6d6a78a94c33b6aaf6e39
[2] https://www.virustotal.com/gui/file/0ca3a4c2800f9454cdcbb8398a7ec97b00f90f4234c7c5e48e206a8352d86750
[3] https://www.virustotal.com/gui/ip-address/194.30.53.68/
[4] https://www.shodan.io/host/194.30.53.68
[5] https://isc.sans.edu/ipinfo/194.30.53.68
[6] https://www.cybereason.com/blog/research/prometei-botnet-exploiting-microsoft-exchange-vulnerabilities
[7] https://blog.talosintelligence.com/prometei-botnet-improves/
———–
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu